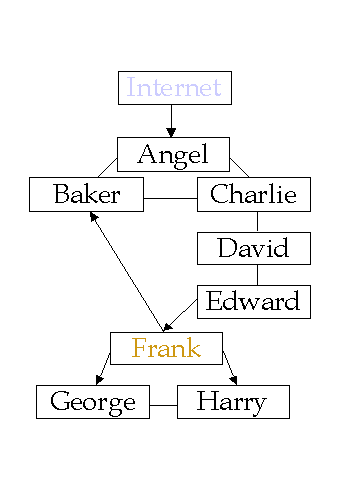
Angel has anomaly detection, path diversity, sensors, waste data
destruction reintegration, improved morality, fine-grained access
control, perception management, integration principle, time, location,
function, and other similar access limitations, security marking and/or
labeling, auditing, and testing.
Baker has fine-grained access control and perception management.
Charlie has background checks, feeding false information, effective
mandatory access control, automated protection checkers and setters, and
trusted applications.
David has time, location, function, and other similar access
limitations, auditing, and uninterruptable power supplies and motor
generators.
Edward has program change logs, trusted applications, and effective
mandatory access control.
Frank has properly prioritized resource usage, trusted system
technologies, and uninterruptable power supplies and motor generators.
George and Harry have no defenses.